How to Use Fortify Static Code Analyzer in Pipelines
The author of this article is EPAM Lead Systems Engineer, Deepanshu Katara.
What is Fortify and what are its benefits?
Fortify is an SCA (static code analyzer) used to find security vulnerabilities in software code.
Fortify SCA provides security as a service to allow testing of vulnerabilities over the code base and as part of the Software Security Assurance program. Fortify can be run with container scanning tools like Snyk. Using this combination means that both the code and container running the code are scanned for vulnerabilities, ensuring a secure vulnerability and assessment testing solution.
Fortify implementation
Fortify SCA executes its vulnerability test by reviewing the JAVA pom.xml file which contains all of the dependencies. Since the scanning is performed at the code level, the best practice is to perform it as early as possible. This is achieved by running the scan after the code checkout. Doing so enables you to stop further processing of the build if vulnerabilities are detected.
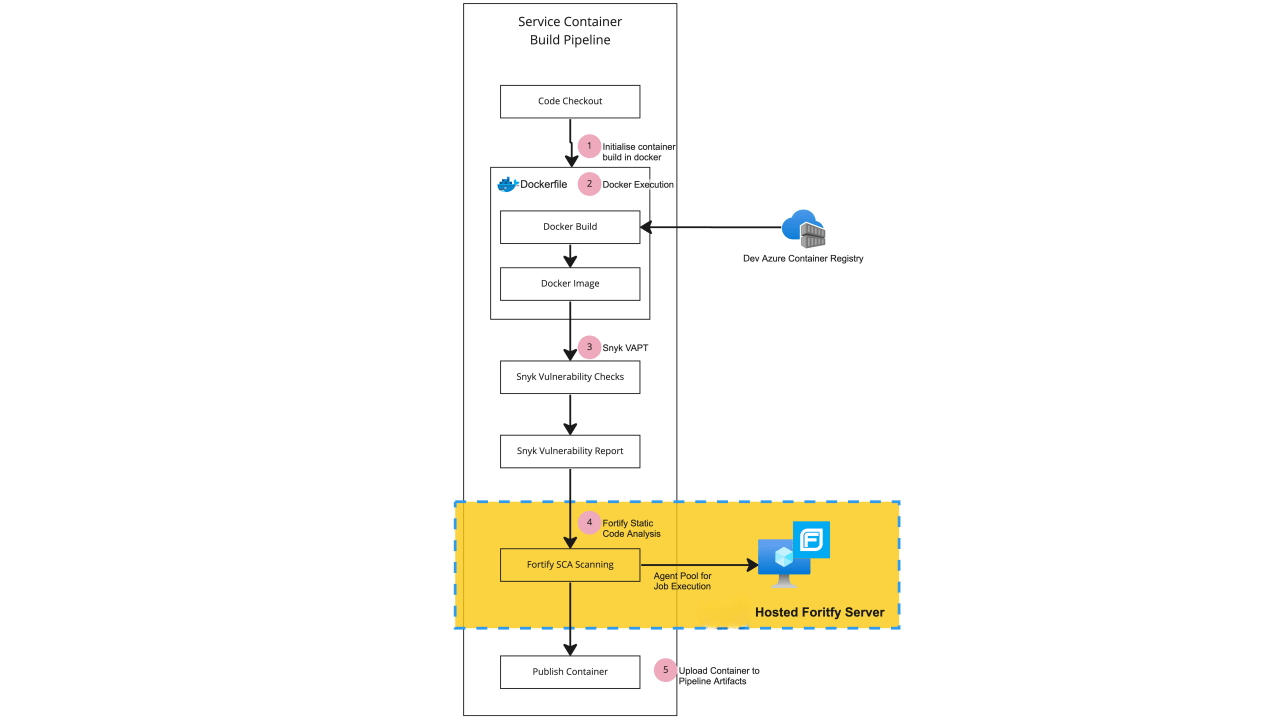
How Fortify works
Fortify works by analyzing Java libraries for any known vulnerabilities. The required installed extension is Micro Focus Fortify. It is a white box testing tool that identifies the root cause of security vulnerabilities and helps remediate them. SAST (static application security testing) solutions analyze an application from the “inside out” and do not read a running system to perform a scan.
To run Fortify, you should be provided with a special agent from your project security team.
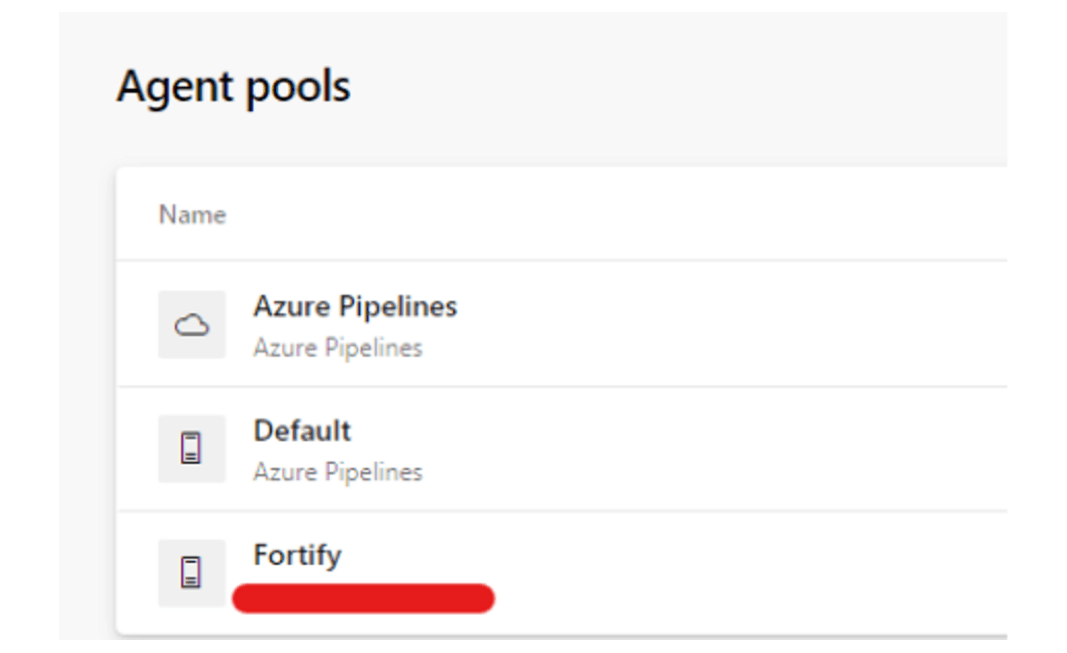
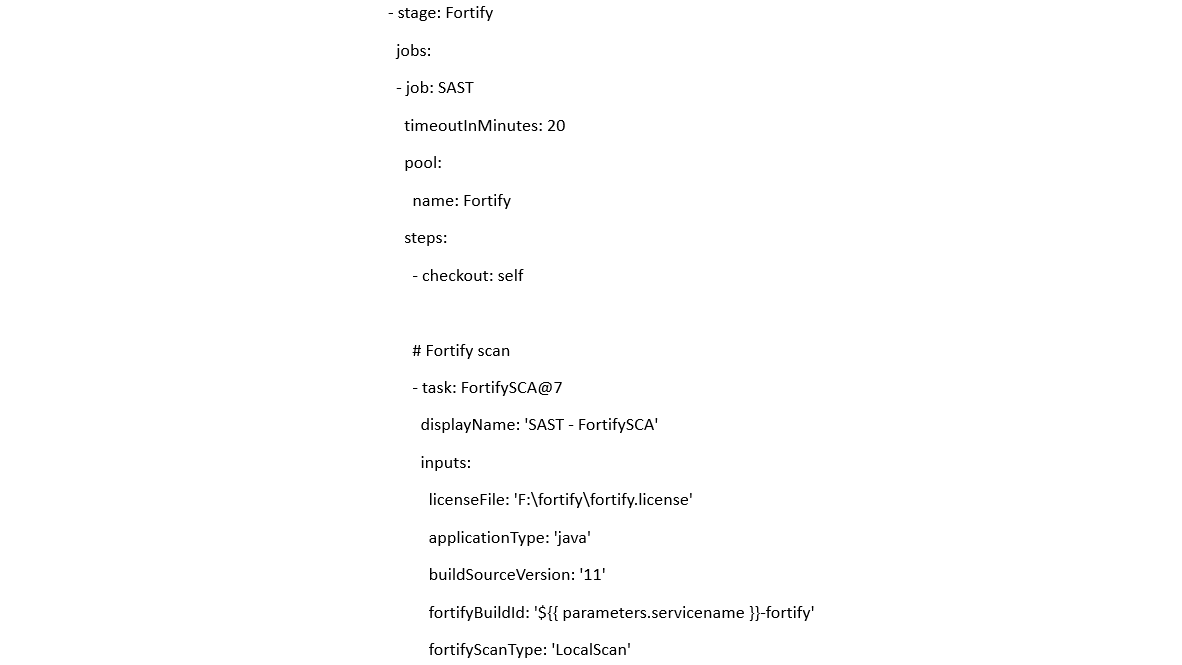
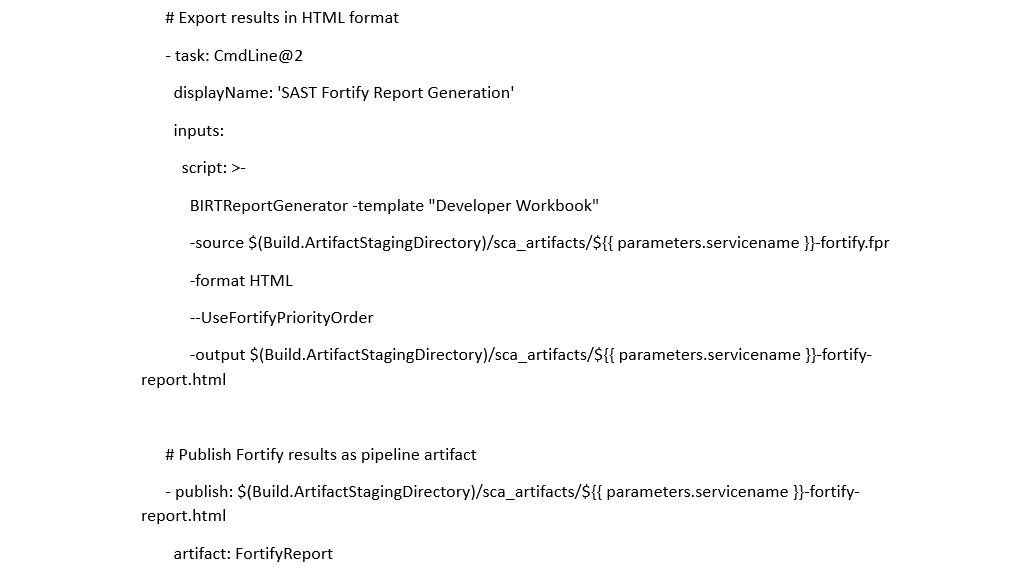
Task usage example in Azure DevOps
Official task documentation page: FortifySCA@7.
Task “SAST Fortify Report Generation” is used for converting scanning results to HTML format.
Limitation
The existing Fortify SCA implementation lacks automatic integration with Azure DevOps for report dissemination. Consequently, verification of Fortify reports requires manual intervention on a predefined schedule.
Recommendations
- Prior to code promotion from the development environment to the quality assurance environment, ensure verification and resolution of reported vulnerabilities.
- Before code promotion from the user acceptance testing to the production environment, verify and address any vulnerabilities identified.
- Coordinate with the information security (InfoSec) team via the DevOps team to establish scheduled dates for manual fetching of reports from the Fortify server.
Conclusion
Fortify SCA has emerged as a pivotal component of the vulnerability assessment pipeline, seamlessly integrated into the DevSecOps framework. Its ability to conduct static application security testing (SAST) by scanning source code and generating comprehensive HTML-based reports enhances the security of applications and contributes to overall stability and reliability. Its versatility extends to both front-end and back-end pipelines, underscoring its relevance across the entire development lifecycle.
Despite Fortify’s importance, it's crucial to acknowledge the need for thorough validation of Fortify reports for critical vulnerabilities, considering the non-blocking nature of the quality gate in the build process.
In summary, Fortify stands as a robust solution — fortifying applications against potential threats, and ensuring heightened security and resilience.
.png)
